WebARX is one of the primary website security systems utilised by Enrapture to protect many of our client websites. This includes those we build and service, as well as though we simply maintain security on for other agencies. The following article ‘Elementor PRO Vulnerability And Attack Analysis’ was published by WebARX on May 8th, 2020. Enrapture does not utilise the Elementor page builder, but we do look after a number of websites for other agencies that have used this solution when developing websites. The article is not meant to disparage the Elementor page builder in any way, but to simply ensure that any security flaws that have recently occurred are fixed.
[Original article published on May 8, 2020 by Agnes Talalaev, www.webarxsecurity.com]
Elementor PRO is a page builder for WordPress with approximately 1 million users. On the 4th of May, many websites had a suspicious subscriber registering to the site that logged in and managed to upload malicious attachments.
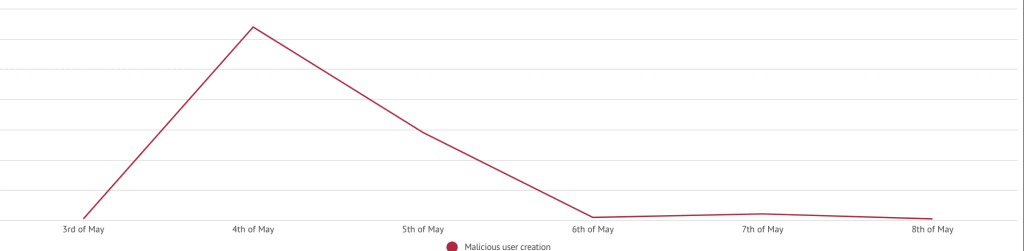
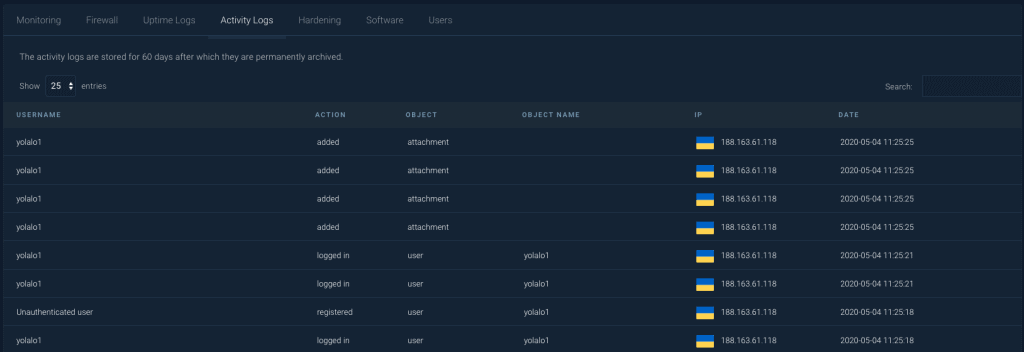
New user registered who instantly uploads multiple attachments.
Split seconds later – another IP was trying to access the attachments:
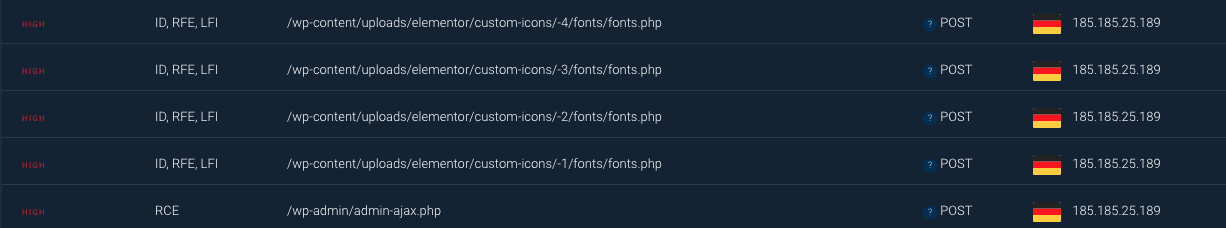
Someone trying to submit POST request directly to the previously uploaded attachments.
The POST request to this backdoor looks something like below. The backdoor allows the malicious user to execute any PHP function with any arguments they specify. In this specific scenario, they uploaded a file to a “tmp” directory with a certain payload which the malicious user can use to verify if the site has been successfully infected.
Array ( [c] => file_put_contents [a] => <?php echo \'abdslk\'.\'dkfjke\'; ?> [f] => /tmp/.... [b] => )
Two different vulnerabilities exploited
The Elementor PRO vulnerability allowed any user to upload malicious files which lead to remote code execution. It was only possible to attack sites that had any kind of registration open (that includes most WooCommerce stores, LMS sites, etc.).
Now the second vulnerability allowed the attacker to remove this limitation. A vulnerability in the Ultimate Addons For Elementor allowed the attacker to create an account, even if registrations were turned off, and continue with the Elementor PRO vulnerability exploitation.
Elementor Pro < 2.9.4 – Authenticated Arbitrary File Upload
The arbitrary upload vulnerability in the Elementor Pro plugin allowed any authenticated user, regardless of their user role, to submit an AJAX request behind the scenes that allowed them to upload any files to the upload directory.
This function was missing a permission check and a proper file extension check which allowed the vulnerability to exist. This in combination with the registration bypass exploit (or open registration on the site), allowed hackers to easily exploit the combination of these issues to upload malware to the site. Since no suspicious payload was involved, most firewalls did not detect anything suspicious.
The issue was fixed in version 2.9.4 which added a permission and file extension check against the upload action.
Ultimate Addons for Elementor < 1.24.2 – Registration Bypass
In order for a malicious user to exploit the arbitrary upload vulnerability, authenticated is required. In case a site does not have registrations open to the public and the Ultimate Addons for Elementor plugin has been installed, they can exploit the registration bypass vulnerability in the plugin to create an account.
This issue exists in the registration form module, which is registered using an AJAX action. This AJAX action was missing 2 checks: whether or not the site allows registrations and whether or not the module itself has been activated by the administrator of the site.
In version 1.24.2 of the Ultimate Addons for Elementor plugin, they added 2 checks: whether or not registrations are open and if the registration form module has been activated. Only if it meets these 2 conditions will it process the request further down the chain.
Steps to take if you think you’ve been affected
First, update both Elementor PRO and Ultimate Addons for Elementor to the latest versions. Next, check the users on your WordPress site and if there are any new or suspicious users. If you have registrations open and many users sign-up to your site on a regular basis, search for the “Subscriber names” we have collected in the IOC section below.
After you have updated the plugins and deleted the malicious users, look at your website’s files and see if there are any PHP or other unwanted files in the /wp-content/uploads/elementor/custom-icons/ directory. Make sure to take a look inside all the folders within /wp-content/uploads/elementor/custom-icons/.
To make sure that the malware hasn’t spread across the website, please follow the guide here.
List of indicators of compromise (IOC)
Here is a list of subscriber, file and folder names with IP addresses that are associated with the attacks.
Subscriber names:
- yolalo1
- yolalo3574
- gjf0xm2v
- wp-cron-not-del-0hr
- wp-cron-not-del-cb7
- wp-cron-not-del-f7j
- wp-cron-not-del-w36
- wp-cron-not-del-zzu
- on
- 15885940386cb25588c011555c7bec26acce4111a4
- 15885955385decf04106c4528236c46cdad57b009f
- 1588596058e1314c335d33ec25c29ad7ad83a2ec97
- 1588598837090fb39cee1ec173efe4961182a8d4ac
- 1588602992ea1cf7b9f1e0344ea9cbf841497a6660
- 1588603357df6a9423800ccefec53dd026ededd48a
- 15886153291bab70f965d0cd889ed8d430e350d3c3
- 15886153568f7d93cb8a13461617e3bc9052790908
- 158861797120b00fc294cdd2dc1c0fea2fd2910918
- 15886225164fe7d694ba2ecfe461d23e57a5cab98f
- 1588628864eadc7723974040025b7e8411d5e5cea3
- 1588631153e14dd423832fd5eb9b453c21faf17c92
- 1588632295892d74341a531e19fad5557bf689badbnew
- 1588635714de7a4c834b40d501d6c4f126b1554eb4
- 158863581865996805da73aec493c498c8df6a4881
- 15886374308667b565a9cab6c160b3601e82ab2e59
- 1588643769b4e2212343fb6467c7e83eef2fb623f3
- 1588649776db8a33272ccd21f180321cf2018e0ab3
- 15886541178cdf19c7f28b6b4cf9dd427d692d5d36
- 15886567682ffdffacab140a4b2f2a644d60257af8
- 1588658484edbd1300fc147db33ed1704aba681667
- 158865903708fd57f1fee54da257ab918466f7fe49
- 15886598300f0d05ca50d361b417c9b775d1ab0bbbnew
- 158866013879811e224f9c32c7cafd88dd2f87f485
- 158866428271c4489f2f1ffce0fc96a97adb467f21
- 1588667387b893ddaf0c8d42c6f5b07c97c603c2bc
- 15886674635acbf16b4ed1dd72d7c587fbc45d364b
- 1588667683c08a39628d59c07e99e9e588ebb348bcnew
- 1588668250f656b3633505d70c9974ff8afe9313f3
- 158866960733cafbc1cdb4912f4c6bf63cb586b161
- 1588672413d79aa2612b769b5f312755c1b40b41e5new
- 1588681886dc17a270c84fc08a4901551d239d0d23
- 1588682784350873375effd75bcfd3e37c232bd190new
- 1588684055caf96aa23c46b9d640ac6228bd860d6
Files within /wp-content/uploads/elementor/custom-icons/:
- wpstaff.php
- demo.html
- Read Mw.txt
- config.json
- icons-reference.html
- selection.json
- fonts.php
IP addresses:
- 188.163.61.118
- 185.185.25.189
- 2a05:8b81:1000:1::946f:8ca8
Timeline:
- May 4th, 2020 – First attacks spotted in the wild
- May 4th 2020 – Vulnerability fixed in Ultimate Addons for Elementor version 1.24.2
- May 7th 2020 – Firewall rules and virtual patches released to all WebARX users
- May 7th 2020 – Vulnerability fixed in Elementor PRO version 2.9.4
Is the Elementor Pro vulnerability patched?
The arbitrary upload vulnerability in the Elementor Pro plugin is patched in version 2.9.4. Firewall rules and virtual patches have been released to all WebARX users.
How critical is the Elementor Pro arbitrary file upload vulnerability?
It is a critical vulnerability that allowed any user to upload malicious files and could lead to remote code execution. It was only possible to attack sites that had any kind of registration open (that includes most WooCommerce stores, LMS sites, etc.).
What to do if my website is hacked?
First, update both Elementor PRO and Ultimate Addons for Elementor to the latest versions. Next, check the users on your WordPress site and if there are any new or suspicious users. If you have registrations open and many users sign-up to your site on a regular basis, search for the “Subscriber names” we have collected in the IOC section below.
After you have updated the plugins and deleted the malicious users, look at your website’s files and see if there are any PHP or other unwanted files in the /wp-content/uploads/elementor/custom-icons/ directory. Make sure to take a look inside all the folders within /wp-content/uploads/elementor/custom-icons/.
To make sure that the malware hasn’t spread across the website, please follow the guide here.
For assistance with this or any other security concerns, contact us as soon as you can.
Original article published on May 8, 2020 by Agnes Talalaev – www.webarxsecurity.com